Comodo Firewall is really a wonderful program to help the endless battle between the data of good quality data and easy evil viruses. I've been using and was very happy with it, but a few days ago, I met many difficulties in removing this firewall to a previous version so I could upgrade to the latest version.
Comodo is a firewall more difficult to remove from a computer. Usually passes through the Add / Remove Programs can not eliminate. You will find the traces that remain in the registry and the real firewall is still recognized by Windows Security Center, not to mention an Internet connection. To get rid of them, you can follow these instructions:
Method 1 (take this in Windows XP as an example)
1. Close all unnecessary programs
2. Temporarily disable the Internet connection
3. Delete the folders and files below, if they still exist. Most users will have C: \ Program Files as default if the location is on another drive, open it.
C: \ Documents and Settings \ All Users \ Application Data Comodo \
C: \ Documents and Settings \ All Users \ Desktop \ COMODO
Firewall Pro
C: \ Documents and Settings \% username% \ Application Data \ Comodo
C: \ Program Files \ [Comodo Firewall folder] Pro
C: \ boot.ini.comodofirewall (this file may not exist).
C: \ WINDOWS \ system32 \ drivers cmdGuard.sys \
C: \ WINDOWS \ system32 \ drivers cmdhlp.sys \
C: \ Windows \ system32 \ drivers inspect.sys \
C: \ WINDOWS \ system32 \ guard32.dll
1. Go to Start - (right click) My Computer - Properties - System Properties - Hardware - Device Manager - View - Show hidden devices - Non-Plug and Play, and then delete all existing entries as below
Comodo Application Engine
Comodo Firewall Pro Helper Driver
Comodo Network Engine.
1. Remove the following registry keys.
HKEY_CURRENT_USER \ Software \ ComodoGroup \ PPC
HKEY_LOCAL_MACHINE \ SOFTWARE \ ComodoGroup \ CDI \ 1
HKEY_LOCAL_MACHINE \ SYSTEM \ ControlSet001 \ cmdAgent Services \
HKEY_LOCAL_MACHINE \ SYSTEM \ ControlSet001 \ Services \ cmdGuard
KEY_LOCAL_MACHINE \ SYSTEM \ ControlSet001 \ cmdHlp Services \
HKEY_LOCAL_MACHINE SYSTEM \ ControlSet001 \ Services \ Inspect
HKEY_LOCAL_MACHINE \ SYSTEM \ ControlSet002 \ Services \ cmdAgent
HKEY_LOCAL_MACHINE \ SYSTEM \ ControlSet002 \ Services \ cmdGuard
KEY_LOCAL_MACHINE \ SYSTEM \ ControlSet002 \ Services \ cmdHlp
HKEY_LOCAL_MACHINE SYSTEM \ ControlSet002 \ Services \ Inspect
KEY_LOCAL_MACHINE \ SYSTEM \ ControlSet003 \ Services \ cmdAgent
HKEY_LOCAL_MACHINE \ SYSTEM \ ControlSet003 \ Services \ cmdGuard
HKEY_LOCAL_MACHINE \ SYSTEM \ ControlSet003 \ Services \ cmdHlp
HKEY_LOCAL_MACHINE SYSTEM \ ControlSet003 \ Services \ Inspect
HKEY_LOCAL_MACHINE \ SYSTEM \ CurrentControlSet \ Services \ cmdAgent
HKEY_LOCAL_MACHINE \ SYSTEM \ CurrentControlSet \ Services \ cmdGuard
HKEY_LOCAL_MACHINE \ SYSTEM \ CurrentControlSet \ Services \ cmdHlp
HKEY_LOCAL_MACHINE SYSTEM \ CurrentControlSet \ Services \ Inspect
HKEY_LOCAL_MACHINE \ SYSTEM \ Software \ Comodo \ Firewall Pro
HKEY_USERS \ S-1-5-21-1202660629-746137067-2145843811-1003 \ Software ComodoGroup \ PPC
HKEY_LOCAL_MACHINE SYSTEM \ ControlSet001 \ Enum \ Root \ LEGACY_CMDAGENT
HKEY_LOCAL_MACHINE SYSTEM \ ControlSet001 \ Enum \ Root \ LEGACY_CMDGUARD
HKEY_LOCAL_MACHINE SYSTEM \ ControlSet001 \ Enum \ Root \ LEGACY_CMDHLP
HKEY_LOCAL_MACHINE SYSTEM \ ControlSet001 \ \ \ Enum Root LEGACY_INSPECT
HKEY_LOCAL_MACHINE SYSTEM \ ControlSet002 \ Enum \ Root \ LEGACY_CMDAGENT
HKEY_LOCAL_MACHINE SYSTEM \ ControlSet002 \ Enum Root \ LEGACY_CMDGUARD
HKEY_LOCAL_MACHINE SYSTEM \ ControlSet002 \ Enum \ Root \ LEGACY_CMDHLP
HKEY_LOCAL_MACHINE SYSTEM \ ControlSet002 \ Enum Root LEGACY_INSPECT
HKEY_LOCAL_MACHINE SYSTEM \ ControlSet003 \ Enum \ Root \ LEGACY_CMDAGENT
HKEY_LOCAL_MACHINE SYSTEM \ ControlSet003 \ Enum Root \ LEGACY_CMDGUARD
HKEY_LOCAL_MACHINE SYSTEM \ ControlSet003 \ Enum \ Root \ LEGACY_CMDHLP
HKEY_LOCAL_MACHINE SYSTEM \ ControlSet003 \ Enum Root LEGACY_INSPECT
HKEY_LOCAL_MACHINE SYSTEM \ CurrentControlSet \ Enum root HKEY_LOCAL_MACHINE \ LEGACY_CMDAGENT \ SYSTEM \ CurrentControlSet \ Enum Root \ LEGACY_CMDGUARD HKEY_LOCAL_MACHINE SYSTEM \ CurrentControlSet \ Enum \ LEGACY_CMDHLP \ Root
HKEY_LOCAL_MACHINE SYSTEM \ CurrentControlSet \ \ Enum Root LEGACY_INSPECT
HKEY_CURRENT_USER \ Software \ Local AppWizard-generated
Applications \ CFP_Setup_3.0.14.276_XP_Vista_x32
HKEY_CURRENT_USER \ Software \ Local AppWizard-generated
Applications \ CFP_Setup_3.0.14.276_XP_Vista_x64
HKEY_CURRENT_USER \ Software \ Local AppWizard-Generated Applications \ CFPLog
HKEY_CURRENT_USER \ Software \ Local AppWizard-generated
Applications \ CPFFileSubmission
HKEY_LOCAL_MACHINE \ SYSTEM \ Software \ Comodo \ Firewall Pro
6. Finally, restart the computer.
Warning: These instructions can modify the Windows registry, and if the transaction is not corrected, may cause serious errors. So if you are unsure of your skill to do it, and if you are a novice with little computer knowledge, it is better to find a good removal tool to help you.
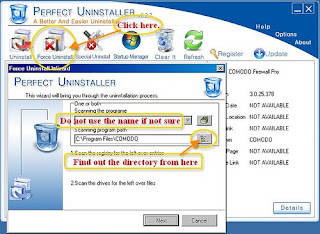
Method 2 Remove Comodo Firewall automatically in seconds
In addition to completely remove the programs, including those that can not be removed from Windows Add / Remove applet, a removal tool far below outstanding features:
uninstall registry entries completely empty or corrupted.
Forcibly removing damaged or hidden agendas.
It is much easier and faster to use than Windows (Add / Remove) application functionality
If you restore the log files.
In fact, there is a removal tool that can help you completely remove Comodo Firewall successfully and ensure that the files all the elements in the now defunct record and are automatically deleted connected with a few clicks. In addition to this software, you can completely remove other programs like Authentium, Norton, Trend Micro Antivirus, Internet Explorer or Microsoft Office and similar programs.
Source from Articlesbase

